What is UTLite 33 exe?
UTLite 33 exe is an executable exe data which comes from the UTLite 33 exe process which comes along with the Customer Tracker Lite 3 3 Software program established by Cisco Systems software application developer.
If the UTLite 33 exe process running in the Windows Operating system is essential, after that you must take care while deleting it. Often UTLite 33 exe procedure may be utilizing CPU or GPU too much. If it is malware or an infection, it may be running in the history without you understanding it.
The.exe extension of the UTLite 33 exe file specifies that it is an executable file for Windows Platforms like Windows XP, Windows 7, Windows 8, and Windows 10
Malware and infections are also sent through exe data. So we have to make certain prior to running any type of unidentified executable data on our computers or laptop computers.
Currently we will certainly inspect if the UTLite 33 exe data is a virus or malware. Whether it should be deleted to keep your computer safe? Find out more below.
Is UTLite 33 exe risk-free to run? Is it an infection or malware?
Allow’s examine the place of this exe data to identify whether this is legit software or a virus. The place of this file and harmful ranking is.
File Area/ Ranking: 72 % dangerous
To check whether the exe documents is legitimate you can begin the Task Supervisor. After that click the columns area and add Verified Endorser as one of the columns.
Now, look at the Verified Signer value for UTLite 33 exe process if it states “Not able to confirm” then the file might be a virus.
| File Call | UTLite 33 exe |
| Software application Programmer | Cisco Equipments |
| File Kind | EXE |
| File Area | 72 % unsafe |
| Software | User Tracker Lite 3 3 |
Over All Scores for UTLite 33 exe: 4/ 5
Next off, check the developer of UTLite 33 exe If the designer of the software program is legitimate, after that it is not a virus or malware. If the designer is not detailed or appears suspicious, you can eliminate it using the uninstall program.
Based on our analysis, we have actually displayed our outcome of whether this UTLite 33 documents is a virus or malware listed below.
Is UTLite 33 exe A Virus or Malware: UTLite 33 exe is not an Infection or Malware.
How to check if UTLite 33 exe is a protection problem?
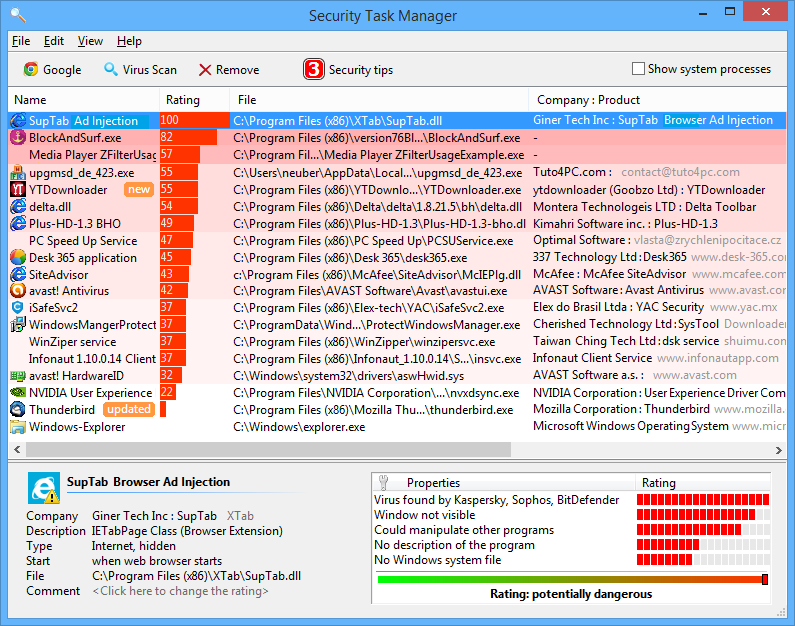
We likewise suggest utilizing the Safety and security job manager application to discover which processes are unwanted in your Windows computer system and can be a security concern. Right here is how you can locate whether UTLite 33 exe is a protection threat utilizing the Protection Job Manager application.
- Download And Install the Security Task Manager application and mount it on your computer system.
- Run it as administrator. It will currently show all the applications that are working on your computer system.
- Currently it will show the Score, data area, business, and product name for every process.
- Currently click on the score column to kind based on rankings.
- You will certainly currently see which process has the most awful rating easily so can make a decision UTLite 33 exe is provided a poor score or not easily.
- You will certainly also locate whether the UTLite 33 exe procedure is essential or otherwise with this feature. Below is a screenshot of the software operating on our home windows computer system.
Exactly how To Eliminate or Uninstall UTLite 33 exe
To get rid of UTLite 33 exe from your computer system do the following steps individually. This will uninstall UTLite 33 exe if it was part of the software set up on your computer.
- If the file belongs to a software application, after that it will likewise have an uninstall program. Then you can run the Uninstaller situated at directory site like C: Program Data>> Cisco Solutions>> Customer Tracker Lite 3 3 > UTLite 33 exe> > UTLite 33 exe_uninstall. exe.
- Or the UTLite 33 exe was mounted using the Windows Installer after that to uninstall it Most likely to System Settings and open Add Or Remove Programs Alternative
- Then Search for UTLite 33 exe or the software program name Individual Tracker Lite 3 3 in the search bar or experiment with the programmer name Cisco Equipment.
- After that click it and choose the Uninstall Program alternative to eliminate UTLite 33 exe documents from your computer system. Now the software program Individual Tracker Lite 3 3 program together with the documents UTLite 33 exe will be removed from your computer.

Regularly Asked Concerns
How do I quit UTLite 33 exe process?
In order to quit the utlite 33 exe process from running you either need to uninstall the program related to the data or if it’s a virus or malware, eliminate it making use of a Malware and Infection elimination tool.
Is UTLite 33 exe an Infection or Malware?
According to the information we have the UTLite 33 exe is not an Infection or Malware. Yet a great file might be infected with malware or a virus to camouflage itself.
Is UTLite 33 exe triggering High Disk Usage?
You can locate this by opening up the Job Supervisor application (Right-click on Windows Taskbar and pick Job Supervisor) and clicking on the Disk option on top to kind and find out the disk usage of UTLite 33 exe.
Is UTLite 33 exe causing High CPU Use?
You can locate this by opening up the Task Manager application and discovering the UTLite 33 procedure and inspecting the CPU use portion.
Just how to inspect GPU Use of UTLite 33 exe?
To inspect UTLite 33 exe GPU usage. Open the Task Manager window and seek the UTLite 33 exe process in the name column and check the GPU use column.
I wish you had the ability to find out more concerning the UTLite 33 exe file and how to remove it. Additionally, share this short article on social media if you find it useful.
Let us know in the comments listed below if you deal with any various other UTLite 33 exe relevant issues.


He is the creator of howtodoninja.com and is an experienced technology writer and a cybersecurity lover with an interest for discovering the current technological improvements. He has 10 years of experience in creating extensive how-to overviews, tutorials, and reviews on software program, equipment, and net services. With a rate of interest in computer system safety, he aims to inform users by composing content on how to make use of technology, and how to also secure their smart tools and individual information from cyber threats. He presently makes use of a Windows computer, and a Macbook Pro, and tests thousands of Android phones for composing his testimonials and overviews.